How FCO-IM with Business Transactions Completes the Picture
Introduction: The Modeling Landscape
Organizations today face a fragmented modeling landscape. Information modelers work with entity relationships or fact-based models. Process modelers create BPMN diagrams or workflow specifications. Software architects develop Event Modeling timelines for event-driven systems. Security architects maintain separate authorization matrices. Each discipline uses different tools, notations, and conceptual frameworks, leading to synchronization challenges and semantic gaps.
What if these apparently distinct concerns are actually different views of the same underlying reality?
Understanding the Foundations
Event Modeling
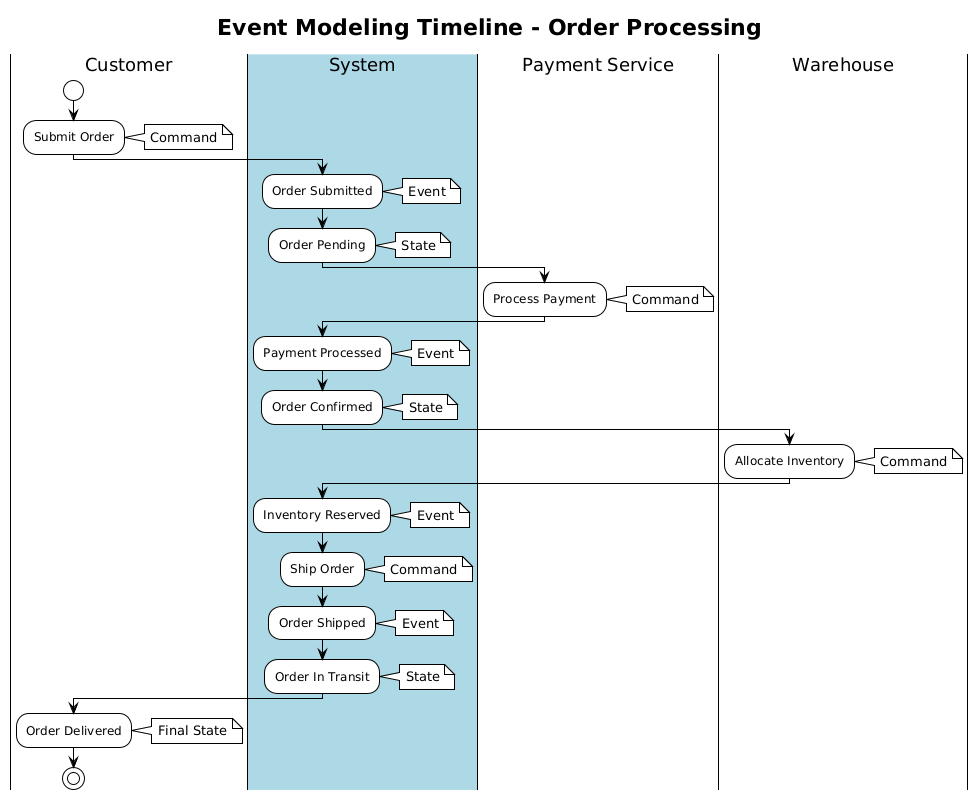
Event Modeling, pioneered by Adam Dymitruk, provides a visual method for designing event-driven systems. Its key components include:
- Events: Facts that have happened, arranged on a timeline
- Commands: Intentions to change system state
- Projections: Read models derived from events
- Swim lanes: Visual rows showing different actors or systems
- Timeline: Horizontal axis representing temporal flow
The method's strength lies in its visual clarity - stakeholders can immediately grasp system behavior by following the timeline narrative. The following diagram illustrates a typical Event Modeling timeline for an order processing system:
FCO-IM
Fact-Oriented Conceptual Information Modeling represents information as elementary facts expressed in natural language. Its foundations include:
- Fact Types: Patterns of facts (e.g., "Person owns Car")
- Object Types: Entities that play roles in facts
- Constraints: Rules governing valid fact populations
- Derivation Rules: Specifications for deriving new facts from existing ones
- Verbalization: Natural language expression of all model elements
FCO-IM's strength lies in its formal rigor - every aspect of the model has precise semantics that can be validated and verified.
The Synthesis: Business Transactions as the Bridge
Modern FCO-IM implementations like CaseTalk introduce several capabilities that enable event-driven modeling:
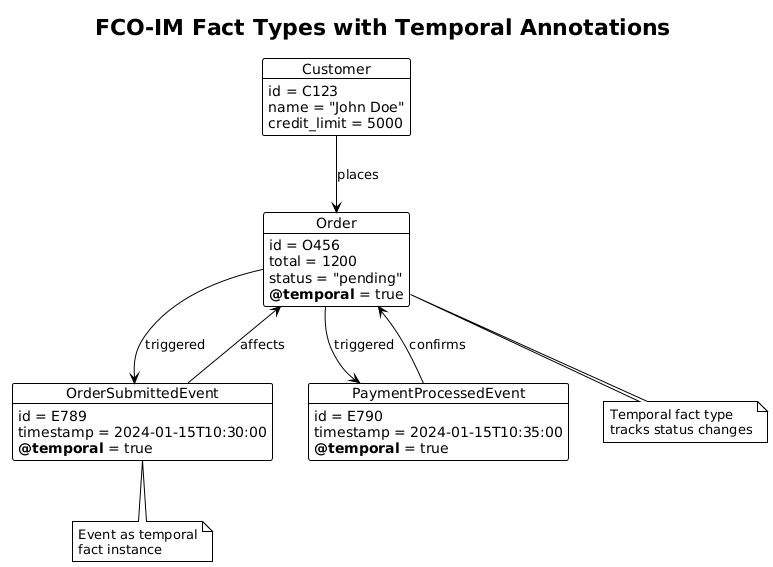
Temporal Annotations
Each Object Type and Fact Type can be annotated with temporal requirements:
- Historical tracking (valid-time and transaction-time)
- State transitions over time
- Temporal constraints and dependencies
These annotations allow FCO-IM to capture not just current state but the complete history of state changes - essentially, an event log.
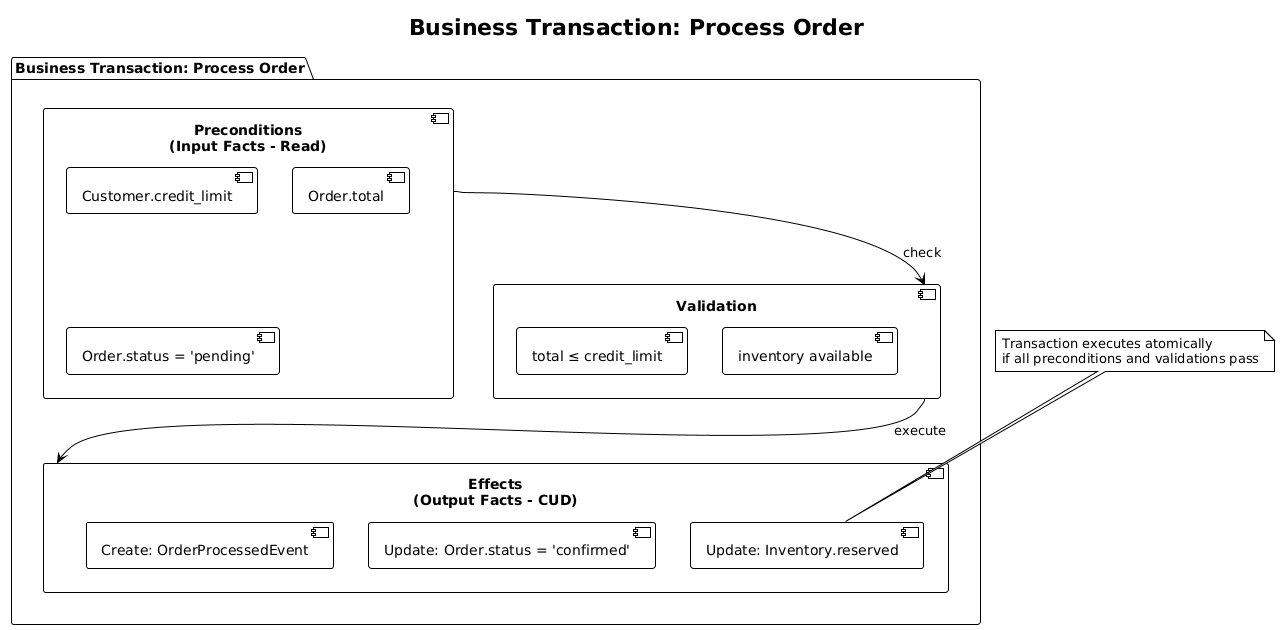
Business Transactions
Business Transactions represent individual process steps with:
- Input fact types: Preconditions that must be read (the 'R' in CRUD)
- Affected fact types: Facts that will be created, updated, or deleted (the 'CUD' in CRUD)
- Execution semantics: Rules for when and how the transaction can execute
This concept provides the crucial link between static information models and dynamic behavior. Here's how a Business Transaction encapsulates preconditions, validations, and effects:
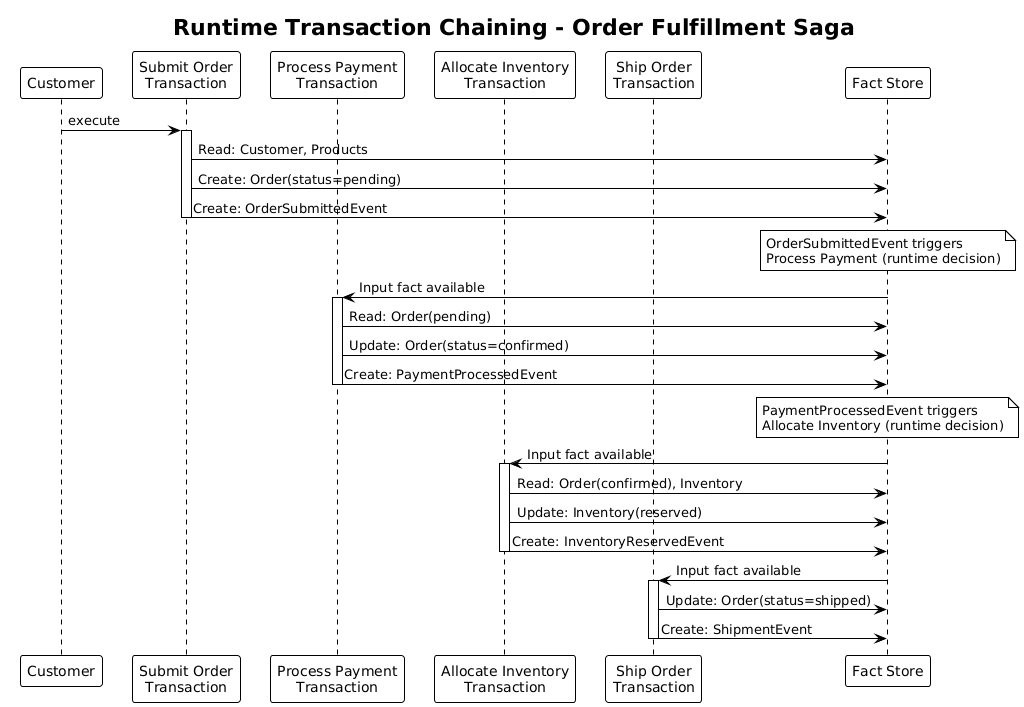
Runtime Chaining
Business Transactions can be chained at runtime based on fact availability:
- Output facts from one transaction become potential inputs for others
- The system determines execution order based on data dependencies
- Complex workflows emerge from simple transaction specifications
The Complete Mapping
With these capabilities, FCO-IM completely encompasses and extends Event Modeling:
| Event Modeling Concept | FCO-IM Equivalent | Additional Capabilities |
|---|---|---|
| Events | Temporal fact type instances | Formal semantics, constraint validation |
| Commands | Business Transactions | Explicit preconditions, atomic guarantees |
| Projections | Derivable fact types | Declarative specification, automatic maintenance |
| State | Current fact population | Complete bi-temporal history |
| Swim lanes | Derived from role permissions | Security-aware, filterable |
| Timeline | Temporal annotation ordering | Multiple time dimensions, branching histories |
Emergent Capabilities
The synthesis provides capabilities beyond either approach alone:
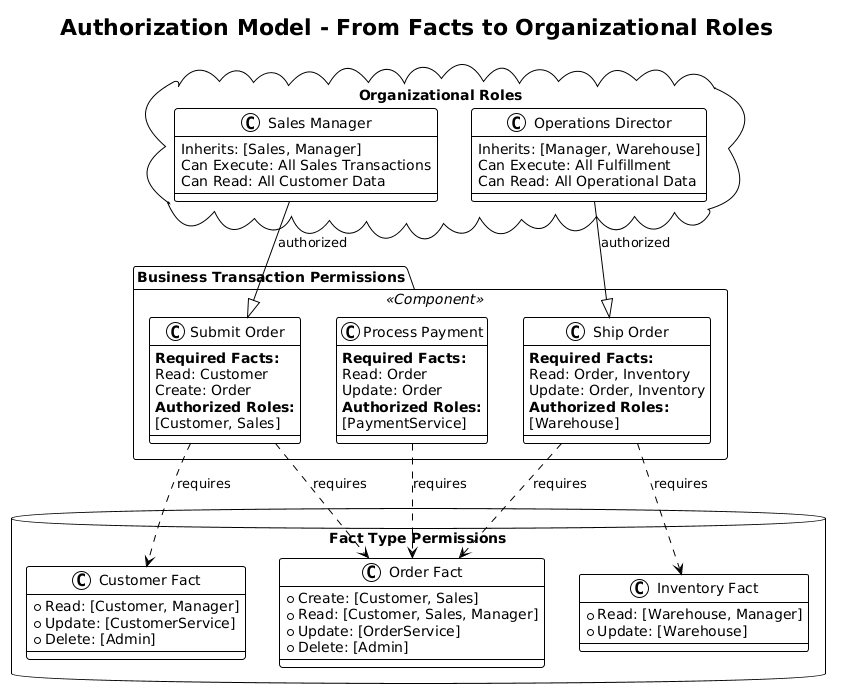
1. Unified Authorization Model
By combining CRUD permissions on fact types with execution permissions on Business Transactions, we get:
- Data-level security: Who can see/modify which facts
- Process-level security: Who can execute which transactions
- Derived constraints: Transaction execution requires appropriate fact permissions
- Organizational governance: Roll up to business capability permissions
The authorization model spans from fine-grained fact permissions to organizational roles:
2. Dynamic Visualization
Swim lane diagrams become derived visualizations rather than primary artifacts:
Role/Actor (from permissions) → Swim lane rows
Temporal sequence (from timestamps) → Horizontal position
Transaction execution (from history) → Event boxes
Data dependencies (from input/output) → Flow arrows
Multiple views can be generated from the same model:
- Specification view (planned behavior)
- Execution view (actual history)
- Authorization view (who can do what)
- Audit view (who did what when)
3. Formal Verification
Unlike traditional Event Modeling, the FCO-IM foundation enables:
- Consistency checking: Verify that transaction chains maintain invariants
- Completeness validation: Ensure all states are reachable/handled
- Deadlock detection: Identify circular dependencies in transaction chains
- Authorization verification: Prove segregation of duties
4. Event Choreography vs. Orchestration
While Event Modeling typically shows orchestrated (centrally controlled) flows, Business Transactions enable choreographed (emergent) behavior:
- Transactions execute when their input facts become available
- No central coordinator required
- More resilient to change and distribution
- Natural fit for microservices and domain-driven design
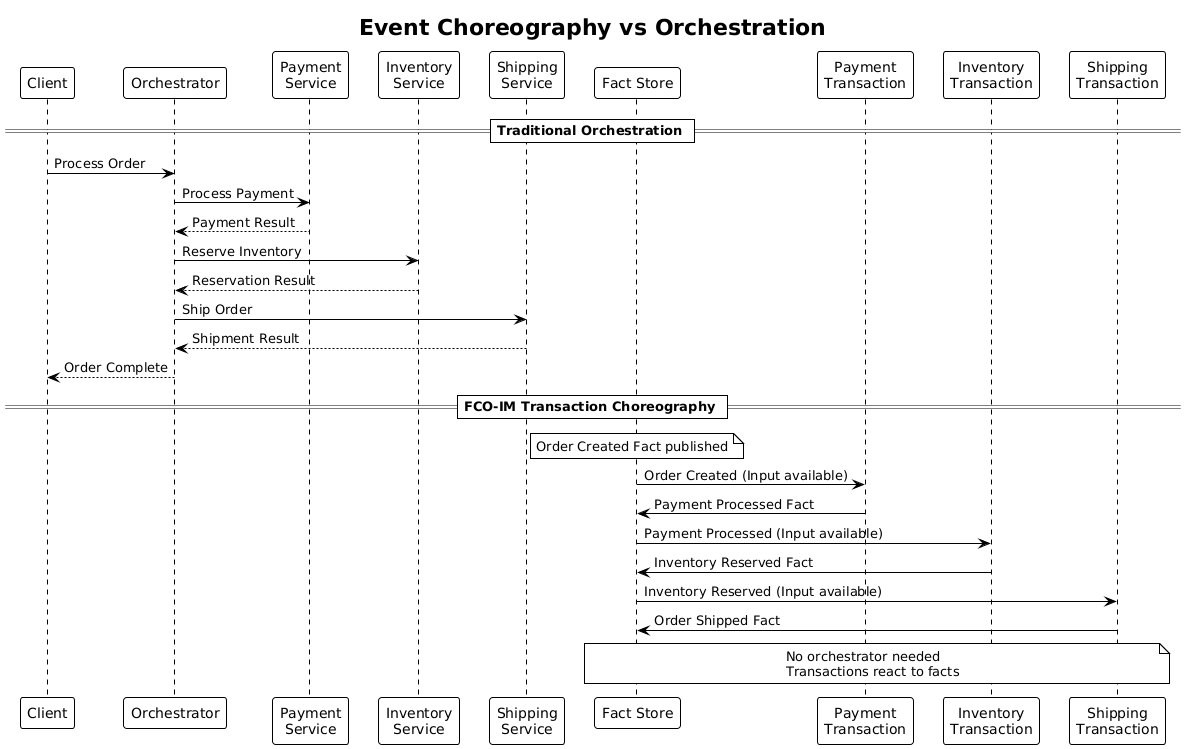
Implementation Patterns
Pattern 1: Command-Event Separation
Business Transaction: "Process Order"
Input Facts (Read):
- Customer[C] has credit limit[L]
- Order[O] has total[T]
- T ≤ L (constraint check)
Output Facts (Create):
- OrderProcessedEvent[E] occurred at[Time]
- OrderProcessedEvent[E] processed Order[O]
- OrderProcessedEvent[E] approved by[System]
Pattern 2: Projection Maintenance
Derivable Fact Type: "Customer Lifetime Value"
Derivation Rule:
Customer[C] has lifetime value[V] :-
V = SUM(Order[O] has total[T]
WHERE Customer[C] placed Order[O]
AND OrderProcessedEvent processed Order[O])
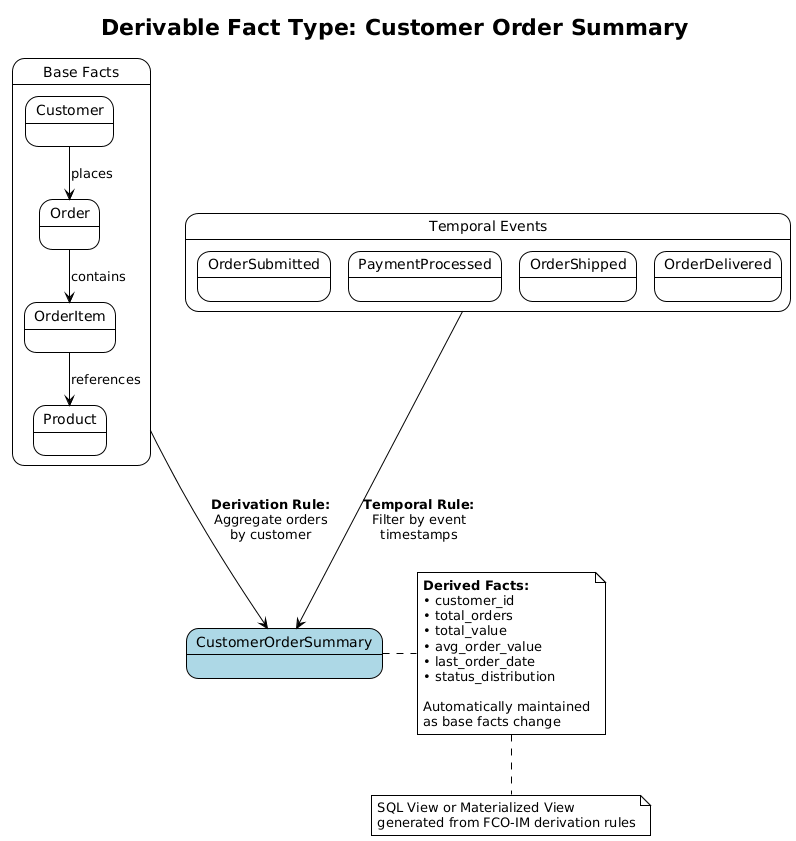
Pattern 3: Saga Implementation
Transaction Chain: "Order Fulfillment Saga"
T1: Process Payment
Input: Order[O] is pending
Output: PaymentProcessed[P] for Order[O]
T2: Reserve Inventory
Input: PaymentProcessed[P] for Order[O]
Output: InventoryReserved[I] for Order[O]
T3: Ship Order
Input: InventoryReserved[I] for Order[O]
Output: OrderShipped[S] for Order[O]
Practical Benefits
For Information Modelers
- Your fact models now capture behavior, not just structure
- Temporal annotations provide complete audit trails
- Business rules enforce both static and dynamic constraints
For Process Modelers
- Processes are grounded in formal data semantics
- No gap between process model and implementation
- Automatic generation of process documentation from fact types
For Event Modelers
- Maintain visual timeline representations
- Gain formal verification of event flows
- Automatic projection maintenance from derivation rules
For Security Architects
- Authorization model derived from the same source of truth
- Complete traceability from data to process to organizational roles
- Compliance reporting generated from the model
Case Study: Order Management System
Consider a typical order management system modeled using this unified approach:
Fact Types (Information Layer):
- Customer places Order
- Order contains Line Item
- Product has inventory level
- Order has status {pending, confirmed, shipped, delivered}
Business Transactions (Process Layer):
- Submit Order: Creates "Order" facts with status "pending"
- Confirm Payment: Updates Order status to "confirmed"
- Allocate Inventory: Creates reservation facts, decrements inventory
- Ship Order: Updates status to "shipped", creates shipment facts
Derivable Facts (Projection Layer):
- Available inventory = Stock level - Reserved quantity
- Customer order history (temporal query)
- Daily sales report (aggregation over temporal facts)
Authorization (Security Layer):
- Customer role: Execute "Submit Order", Read own orders
- Payment role: Execute "Confirm Payment", Read payment facts
- Warehouse role: Execute "Allocate Inventory", "Ship Order"
- Manager role: Read all derived reports
From this single model, we can generate:
- Event Modeling timeline visualization
- BPMN process diagram
- Entity-relationship diagram
- Authorization matrix
- API specifications
- Database schema with row-level security
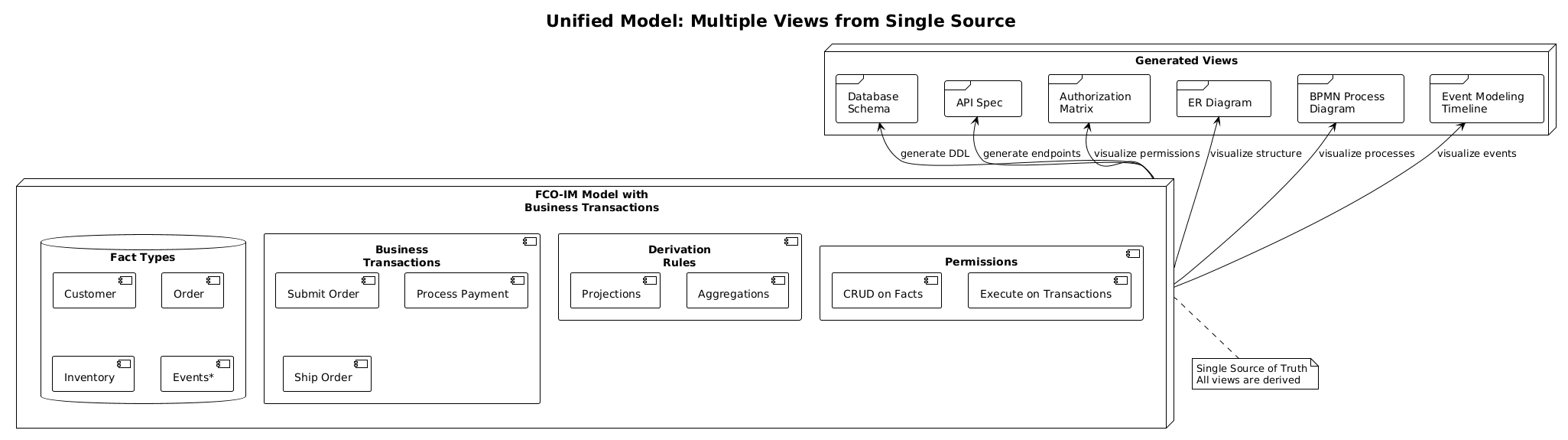
Comparison with Alternative Approaches
vs. Pure Event Modeling
- Advantage: Formal semantics enable verification and validation
- Advantage: Authorization is intrinsic, not bolted on
- Advantage: Multiple views from single model
- Trade-off: Requires more upfront rigor in modeling
vs. BPMN + Data Models
- Advantage: No synchronization between process and data models
- Advantage: Process emerges from data dependencies
- Trade-off: Less suitable for human-centric workflows
vs. Event Sourcing Alone
- Advantage: Declarative projections vs. coded event handlers
- Advantage: Business-level modeling vs. technical implementation
- Trade-off: Requires FCO-IM tooling support
Future Directions
This unified approach opens several avenues for advancement:
Tool Development
- Automatic generation of Event Modeling visualizations from FCO-IM models
- Real-time collaboration on temporal fact models
- Simulation of Business Transaction execution
Methodological Extensions
- Patterns for common event-driven architectures
- Guidelines for modeling distributed systems
- Integration with domain-driven design concepts
Formal Methods
- Temporal logic verification of transaction chains
- Automated testing generation from fact type constraints
- Proof of security properties from authorization rules
Conclusion
The integration of FCO-IM with Business Transactions and temporal annotations provides a complete modeling solution that unifies traditionally separate concerns. Rather than choosing between information modeling, process modeling, and event modeling, we can have all three as different views of a single, formally grounded model.
This approach offers several key advantages:
- Single source of truth: One model generates all views
- Formal rigor: Mathematical foundation for verification
- Visual clarity: Timeline visualizations for stakeholder communication
- Complete authorization: Security from data to process to organization
- Runtime flexibility: Choreographed rather than orchestrated processes
For organizations struggling with modeling fragmentation, this unified approach promises reduced complexity, improved consistency, and better alignment between business and technical perspectives. The swim lanes of Event Modeling become a visualization choice rather than a modeling constraint. Process flows emerge from data dependencies rather than being separately specified. Authorization permeates the entire model rather than being an afterthought.
As Adam Dymitruk noted about Event Modeling: "The simplicity is the power." By grounding this simplicity in FCO-IM's formal rigor, we achieve both power and precision - a combination that has long been the holy grail of system modeling.
The future of system modeling may not require choosing between different approaches but rather recognizing that information, events, processes, and authorization are simply different perspectives on the same underlying business reality. FCO-IM with Business Transactions provides the foundation for capturing this reality in all its richness.